Gartner Inc. predicted that by 2023, CIOs would be responsible for over three times the endpoints they were responsible for in 2018 due to the rapid evolution of IoT trends and technologies. With billions of physical devices worldwide connected to the internet today, this prediction is on its way to coming true. However, the rapid […]
7 Questions to Ask When Evaluating MSPs Having an up-to-date technology infrastructure is critical for organizations to perform well in this ever-changing business environment. An outdated technology infrastructure can harm your business by: Giving cybercriminals a free pass Putting your company in hot water with regulators Reducing overall productivity Causing employee dissatisfaction Upsetting your customers […]
3 Benefits of Conducting a Technology Audit When was the last time you conducted a comprehensive technology audit? If it’s been a while or hasn’t happened at all, this means you’re probably vulnerable to a cyberattack. Cybercrime shows no signs of slowing down and is expected to cost the world $10.5 trillion per year by […]
Over the last year, many organizations struggled to keep their private data secure against cyberthreats as they rushed to adapt to pandemic-inspired shifts in workforce and operations. Cybercrime is becoming increasingly prevalent, and the sophistication and volume of cyberattacks is escalating as well. According to a Statista report, over 300 million ransomware attacks occurred in […]
The importance of data privacy and data security has grown exponentially as organizations today collect and store more information than ever before. Having a robust data protection strategy is critical to safeguard confidential information and to ensure smooth functioning of your business. But before we move on, let’s take a step back to understand the […]
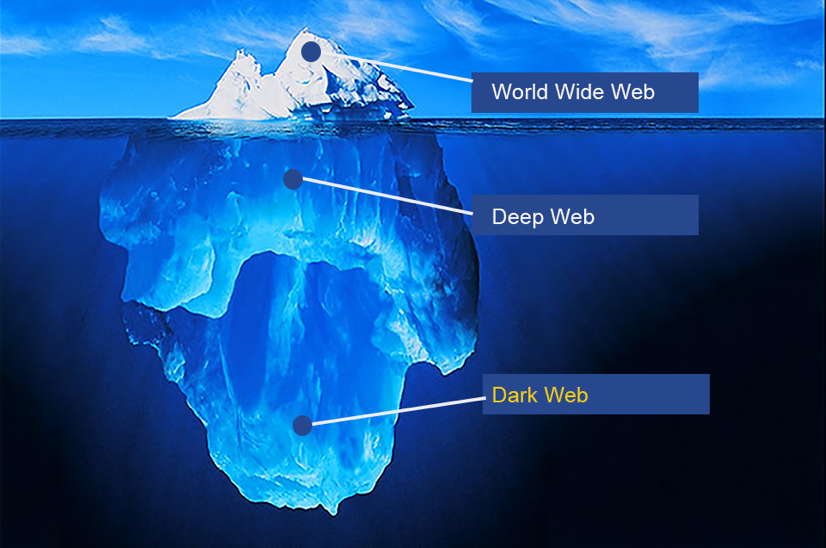
Identity theft is an unfortunate occurrence that is all too familiar with most business owners, but do those individuals know where the compromised data will end up? Often, these business owners are unaware of the virtual marketplace where stolen data is purchased and sold by cybercriminals; a place known as the “Dark Web”. What […]
Phishing Campaigns and other cyberattacks at work. Every now and then, an email with a catchy subject line appears in your inbox and you end up clicking on it, either because you’re curious about the subject line or because you assume the sender is trustworthy. Unfortunately, this is how most cyberattacks tend to begin – with a […]
MS Tech Solutions, a Jamaican-based multinational information technology company, has sought to satisfy the market for information technology (IT) specialists by training the next generation of software enthusiasts. In recent years, the demand for careers in IT has skyrocketed, with analysts indicating that there are nearly five million vacancies in the cybersecurity field alone. Through […]
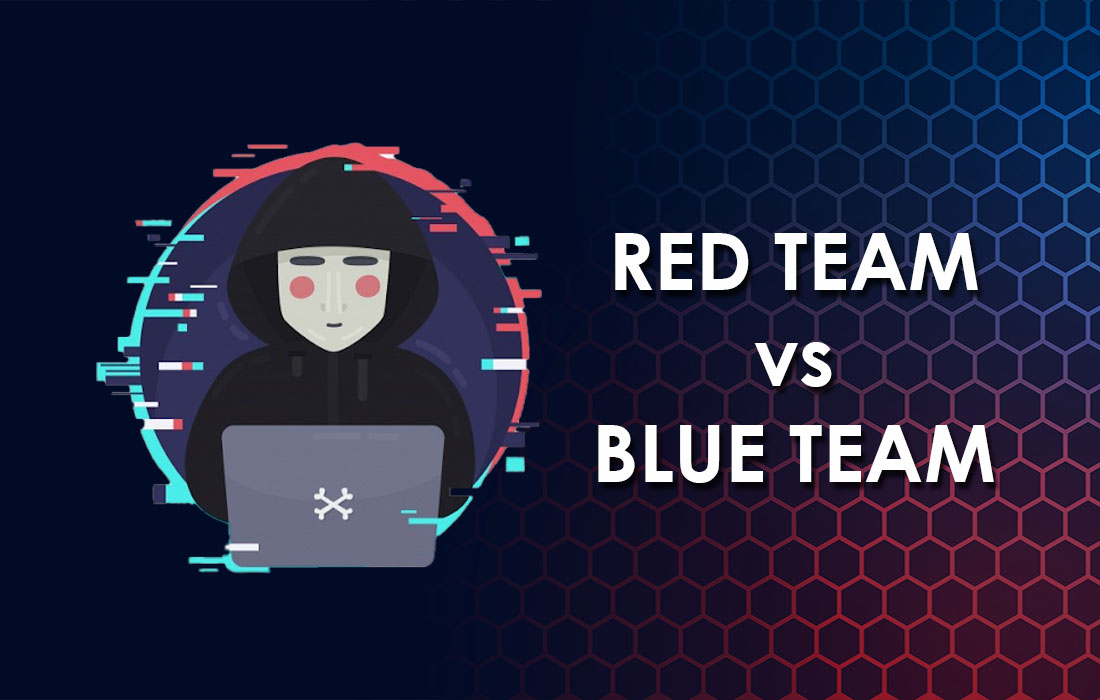
Why You Need Purple Team Services to Protect Your Business from Cyber Attacks. The terms “red team” and “blue team” are often used when we discuss cybersecurity. In this ceasefire approach, the red team is the attacker that tries to infiltrate an organization’s digital and physical defenses using any attacking technique available to the attackers. […]
Cybersecurity can be understood as IT protection. It is a process of securing systems, servers, mobile devices and other automated systems from malicious attacks. On average, it can take up to 6 months to detect a data breach. Implementing cybersecurity protocols for your business will keep your networks and sensitive data safe from cyber attacks. […]