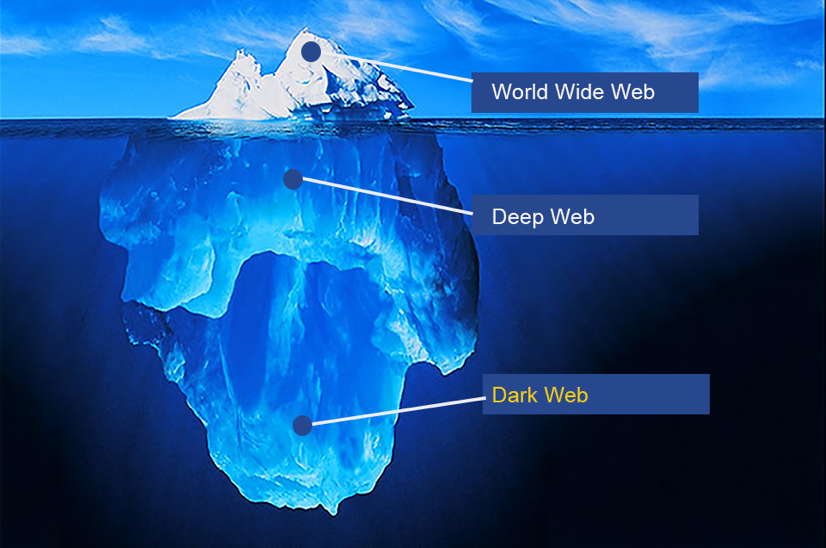
Identity theft is an unfortunate occurrence that is all too familiar with most business owners, but do those individuals know where the compromised data will end up? Often, these business owners are unaware of the virtual marketplace where stolen data is purchased and sold by cybercriminals; a place known as the “Dark Web”. What […]
Phishing Campaigns and other cyberattacks at work. Every now and then, an email with a catchy subject line appears in your inbox and you end up clicking on it, either because you’re curious about the subject line or because you assume the sender is trustworthy. Unfortunately, this is how most cyberattacks tend to begin – with a […]
Cybersecurity can be understood as IT protection. It is a process of securing systems, servers, mobile devices and other automated systems from malicious attacks. On average, it can take up to 6 months to detect a data breach. Implementing cybersecurity protocols for your business will keep your networks and sensitive data safe from cyber attacks. […]